Security

Archibus Cloud is a solution you can count on when security is paramount. Below you can find out in detail how we ensure the level of security in different situations in our Cloud services.
With Archibus Enterprise SaaS (Customizable Archibus Enterprise delivered as Software as a Service) you can implement added features to your projects to keep the highest levels of security.
If you have any additional questions you can contact us.
ARCHIBUS Hosting Services: hosting architecture
Built from experience, focused on security and performance
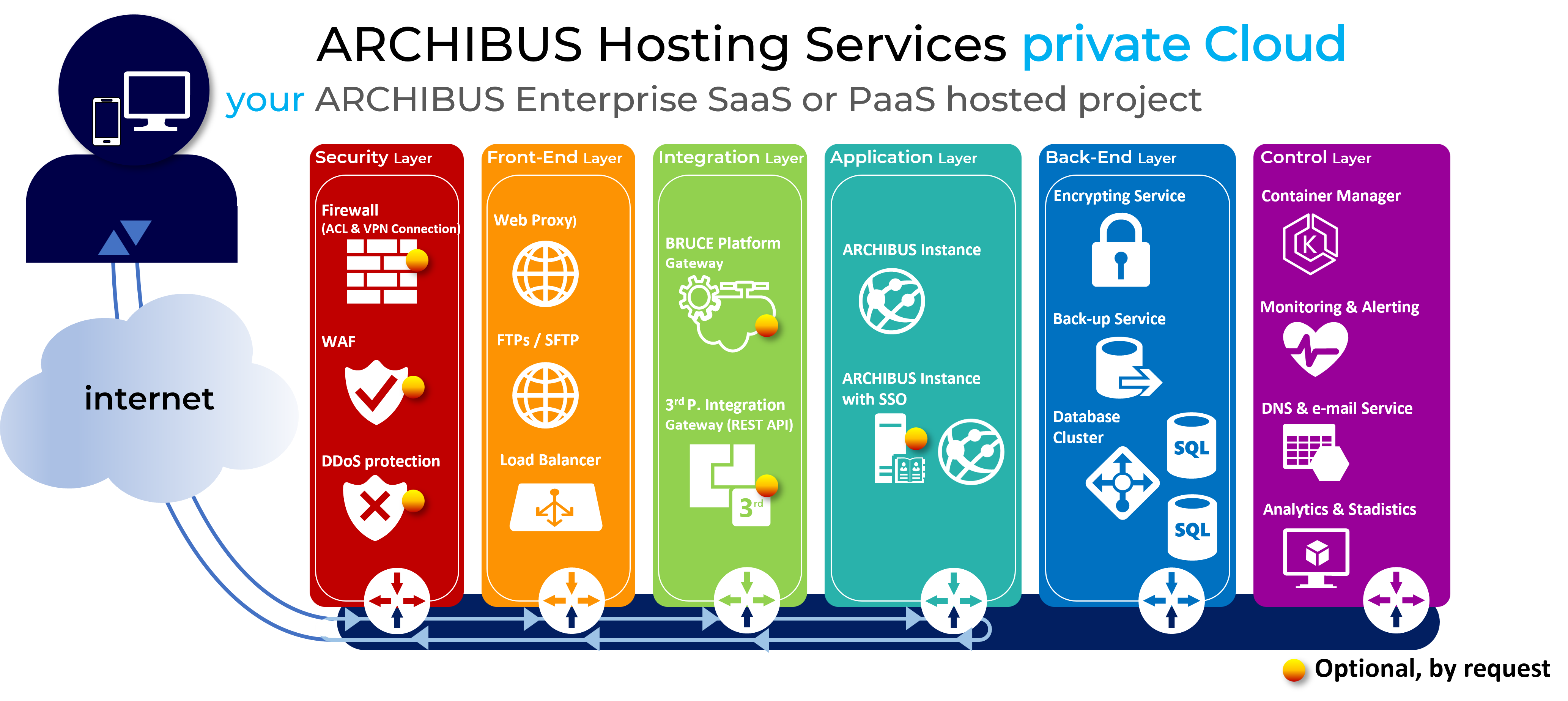
ARCHIBUS Hosting Services Security Details
1 ASC-HS Infrastructure
The projects delivered by ARCHIBUS Hosting Services (ASC-HS) are hosted in “ARCHIBUS Authorized Hosting Partners” secure, top-tier data centers.
The “ARCHIBUS Authorized Hosting Partners” (Amazon Web Services – AWS, Azure, IBM Cloud, and ORACLE Cloud):
- provide Service Level Agreements (SLAs) aligned with the SLAs provided and committed by ASC-HS for power and environmental systems through a number of redundant subsystems, including power and fiber trunks from distinct sources.
- offer a highly secure and reliable carrier-neutral environment to deploy computing, network, storage and IT infrastructure. World-class data centers help reduce the capital and operational expense required to house and protect applications and systems.
- Managed Network and Connectivity services include the most basic layer one services such as physical interconnection all the way through more complex layer three monitoring of networks and alerts. Carrier-neutral design provides zero mile access to robust connectivity and at the same time delivers cost savings, flexibility, and can scale to match customer growth while still delivering the performance customers demand.
Our outsourced data centers offers a full line of managed and professional network security solutions, including vulnerability assessments, penetration testing, incident response and customized services to help clients identify, understand, and effectively deal with security issues before and after they occur.
1.1 Security Data and Certifications.
Our hosting providers are certified according to ISO27001 or SAS70 standards. They accomplish with the security rules and follow the rules data protection policies according to EU Directive 95/46/EC.
ARCHIBUS Hosting Services are based on ARCHIBUS, a TIFM (Total Infrastructure and Facilities Management) solution. Depending on the contracted applications or modules, all the loaded data in ARCHIBUS Hosting Services system is related with customer’s infrastructure and general customer’s data which identifies companies. Some examples are: Company name, contact customer name, contact customer last name, address, telephone, mail, etc. ARCHIBUS Hosting Services also can load general employee information.
1.2 Information Security
ASC-HS datacenter has implemented controls to provide network based security measures to protect its enterprise network. A security policy is in place and a security awareness program is designed to educate employees to protect ASC-HS’s network and systems. A variety of hardware and software based tools have been deployed, which include firewalls, intrusion detection systems, routers, switches, real-time monitoring, and audit logging.
Redundant and clustered industry standard firewalls, switches and routers are implemented to provide a high level of availability and security of network, applications and data. In clustered firewall/router implementations, if one system fails, data traffic is automatically routed to the other standby firewall/router. Configuration standards of firewalls and routers are documented. The configuration of the firewall systems follow vendor recommendations and are based on the principle of least privilege, which allows only necessary and authorized access and denies other services and protocols. The firewalls are strategically placed on the network to filter data packets according to predefined access rules. Administrative access to networking devices is limited to authorized IT personnel only.
The enterprise network is segmented and grouped into different virtual local area networks (VLAN) based on business functions and responsibilities. The VLANs are built by deploying industry standard switches and the proper configuration and administration. Network segmentation serves as an additional security measure to minimize risks resulting from unauthorized network access.
A third party company is engaged to perform quarterly vulnerability assessments for a portion of its publicly accessible IP addresses. The IT personnel review the scanning reports to assess and remediate potential network and system vulnerabilities.
The ASC-HS’s team performs annual penetration tests scan against the management environment and reviews the results and remedies potential network and system vulnerabilities.
1.3 Security Incident response
ASC-HS maintains a security incident response plan in order to organize resources to respond in an effective and efficient manner to an adverse event related to the safety and security of a computer resource under ASC-HS’s management. An adverse event may be malicious code attack, unauthorized access to managed networks or systems, unauthorized utilization of ASC-HS services, denial of service attack, or general misuse of systems.
An incident response team is in place with defined roles and responsibilities. The purpose of this team is to protect ASC-HS and its customers’ information assets, provide a central organization to handle Incidents, comply with government or other regulations, prevent use of ASC-HS managed systems in attacks against other systems, and minimize the potential for negative exposure. Major responsibilities of this team include:
- Limiting immediate incident impact to customers and business partners
- Recovering from the incident
- Determining how the incident occurred
- Determining how to avoid further exploitation of the same vulnerability
- Avoiding escalation and further incidents
- Assessing the impact and damage
- Determining the cause of the incident
- Compiling and organizing incident documentation
- Reviewing response to incidents
- Updating policies and the Security Incident Response Plan
Security incident occurrences are tracked and documentation is maintained. Actions and procedures are documented to guide the incident response team to respond in the event of a security incident and include:
- Taking control of the incident and invoking the security incident response plan
- Assigning an incident response coordinator, communication manager, and technical account manager and starting documentation of the incident report including personnel assignments
- Notifying the security manager on duty at the time of the incident
- Assessing the incident
- Reporting findings to the communications manager
- Communicating the incident to the incident response team, customer, and identified additional personnel including external agencies as appropriate, and maintaining communications throughout the life of the incident
- Containing the damage and minimizing immediate exposure
- Identifying the impact of the incident
- Remediation of the vulnerabilities
- Collecting and protecting evidence
- Recovering the systems
- Preparing the incident analysis report for trending and analysis
- Preparing and presenting the incident summary as necessary to the customer
Once the documentation and recovery phases of the incident are complete, the team thoroughly reviews the process that was followed during the incident to determine what was successful and where mistakes were made. Based on findings, policies and the plan are updated as appropriate.
1.4 Infrastructure system monitoring and support
Our hosting providers provide monitoring 24/7/365 of ASC-HS and clients’ networks and system infrastructure for continuous system performance and signals of system failure.
The ASC-HS providers tests monitoring redundancy several times each day. Another method of monitoring notification specifically for network engineers includes alerts firing through the network monitoring information system (NMIS). When an alert fires in NMIS, an e-mail is sent to the network operations engineer team.
A shift manager is on duty to provide proper supervision on each shift during the week and is on call on weekends if issues arise. A monitoring engineer cannot leave his/her monitoring station until being replaced with another monitoring engineer.
The system performance items monitored by the ASC-HS include:
- Disk space usage, CPU, memory, NIC utilization, back up successes and failures
- Thresholds for CPU utilization, networking device interface utilization, and interface up/down status
- Keyword monitoring (URL and IP), ping-based connectivity monitoring for all devices
- Server hardware monitoring, predictive fault detection
When an alert is triggered, a monitoring engineer creates and assigns a service call to the team responsible for responding to the incident. All engineers take actions following alert handling procedures and incident resolution procedures. The incidents are tracked to resolution using service calls within the support console.
1.5 System Data Backup Procedures
ASC-HS backs up the files and data on all servers in order to ensure a fast recovery of services in the event of a hardware/software failure or physical disaster. To make these services available, the files on each system are regularly copied to a recovery storage medium and retained for various periods of time. ASC-HS has established formal procedures to manage data backup and backup media operations.
ASC-HS uses the following backup schedules:
- Weekly full backups are run according to the server backup schedules. The weekly full backup tapes are clearly labeled and kept onsite in fireproof containers for two weeks.
- Daily incremental backups are run each day between the regularly scheduled full backups. The daily incremental backup tapes are clearly labeled and stored onsite for easy and fast recovery.
The backup is automated using third party backup software utilities, which provide reports on successful and failed jobs, status and run times. A backup verification process is run on each file after the backup occurs to ensure the data integrity of the tape. The daily backup job status for each system is monitored and service calls are created in service desk for every failure or exception reported by the backup process.
The customer support incident management team provides Level 1 support for standard backup failures and escalates to Level 2 if they are unable to resolve the problem. Exceptions to this standard backup process are documented in the return to service documentation specific to customer systems as applicable. This procedure allows systems to be restored in the event of a disaster. Individual files can be restored if they were present on the system during a backup operation.
Backup tapes are replaced when an error due to bad media is detected during the backup process. Any defective media, including defective tapes, are logged into the Tape Disposal Log and dispatched for physical destruction. RAID (Redundant Array of Independent Disks) technologies are implemented according to customers” requirements to reduce the risk that a disk problem could bring down the entire system.
- Backups are done when servers are at their minimum activity period in order not to interfere with their current performance.
- One daily completed backup should be done.
- Fortnightly copies are stored; therefore data can be restored as it was any previous day before backup was done.
1.6 System Software Maintenance
ASC-HS utilizes many information system software products from a variety of vendors. These software products include operating system software, database system software, networking system software and other middleware applications. Software product vendors produce new releases, service packs, and hot-fixes to enhance the software’s functionality and security. It is important for ASC-HS to be notified of, evaluate, package, test, and implement vendor patches and updates to maintain a high level of functionality and security of its network and hosted systems for clients. ASC-HS has established a
patch management process to guide evaluation, testing, and implementation of vendor system software patches.
ASC-HS’s Team is notified of software updates in several ways including vendor provided automatic system update services, vendor notification mailing lists, and industry-specific mailing lists. For example, new security patches for the Microsoft platform are released the second Tuesday of each month. Once these patches are released, ASC-HS receives an e-mail notification from Microsoft.
Microsoft also sends ASC-HS an e-mail notification of any emergency patches released prior to the second Tuesday of each month. Another example, ARCHIBUS send an e-email with notification of the software updates.
ASC-HS evaluates the criticality and applicability of the updates. Based on the rating of the patch by the vendors and how it affects the hosted server-based solutions, ASC-HS determines whether the patch is required or not.
Each patch is tested in a non-production environment to ensure the patch’s functionality and operability with the standard system settings. The technical people group then creates a report detailing an advisory of possible effects, installation procedures, and back-out procedures to guide patch implementation on production systems. Once testing is complete, the patches are released to Change Management for scheduling and deployment to production. The actual patch installation follows ASC-HS’s change management procedures.
1.7 ARCHIBUS Hosting Services Deployment
All applications are installed on an additional partition which is independent of the operating system default C:\)
The deployment workflow is:
- (optional) DEVELOPMENT Server – Remotely accessible with all the control (Web + Terminal Server Admin) by ARCHIBUS Business Partner (Implementer).
- (optional) QUALITY ASSURANCE Server – To test all changes in the projects before PRODUCTION – Remotely accessible by End Customer (Web) and ARCHIBUS Business Partner (Web + Terminal Server Admin)
- PRODUCTION Server – Only accessible through FTP and Web, directly to ARCHIBUS Web Central Project. Project is isolated in its own Application Server. In this scenario the Database is allocated in an external database server.
- (optional) DATABASE Cluster – This infrastructure, is an external cluster (MS SQL Server or Oracle) to host Project Databases.
Archibus Solution Centre Hosting Services OU
Valukoja 8 – 8 and 13. floor, B-lift
11415 Tallinn – Estonia – EU
Content

Company


